Policy Management
Mastering Policy Navigation: Explore Categories, Websites, Geolocation, and Settings. Unlock the Potential of Global Policies to Effortlessly Cascade Changes, While Adapting with Ease to Diverse Customer Needs.
Quick Navigation
Categories | Websites | Geolocation | Settings | Isolation | Global Policy Management
---------
Welcome to the world of efficient DNS filtering management! This guide takes you through a seamless process to set up a comprehensive policy, ensuring a secure and tailored online experience for your customers. Learn to control access by category, website, and geolocation, and harness the strength of global policies for effortless changes.
Policy Configuration
A Filtering policy is a set of predefined rules that govern how a device or network handles DNS queries. It controls website access, content filtering, and security measures, ensuring tailored online experiences and protecting networks from malicious content.
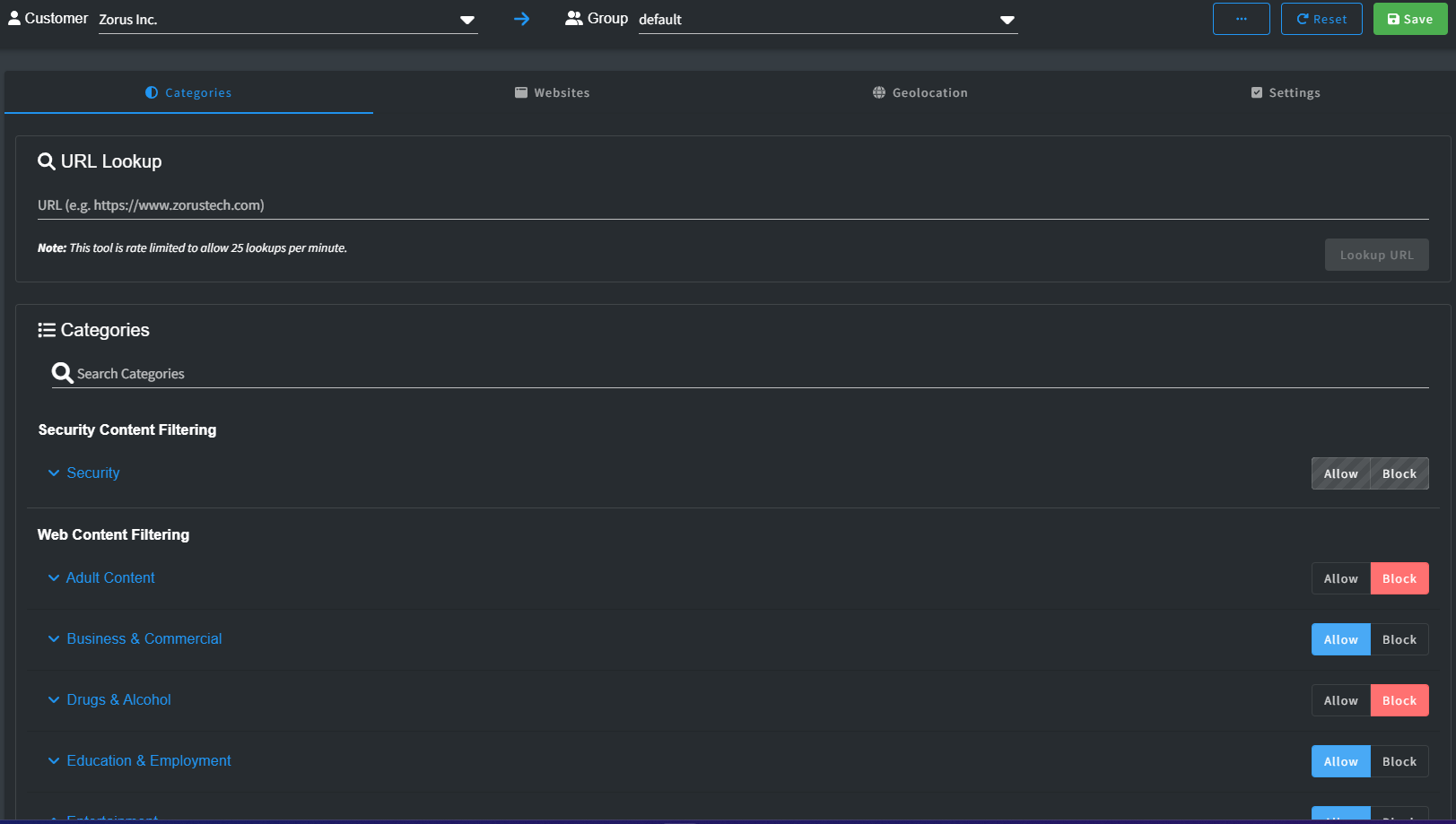
Categories
Categories organize websites based on content, purpose, or type using a special threat intelligence system. This helps filter internet access, letting admins allow or block sites based on criteria like education, entertainment, social media, or adult content.
Categorization is split into Security and Web Content sections, where Security bolsters customer safety by fending off threats, malware, and viruses. Meanwhile, Web Content oversees approved sites and reduces distractions.
Unveil the power of Zorus's comprehensive control with an array of over 175 sub-categories meticulously structured within broader segments. Benefit from the adaptability of detailed or general settings, simplifying management and personalization for your Customers needs.
When uniformity reigns among sub-category options (Allow or Block), the Category reflects that consensus. However, in the case of varied sub-category settings, stripes emerge, encouraging exploration to uncover specific differentiations.
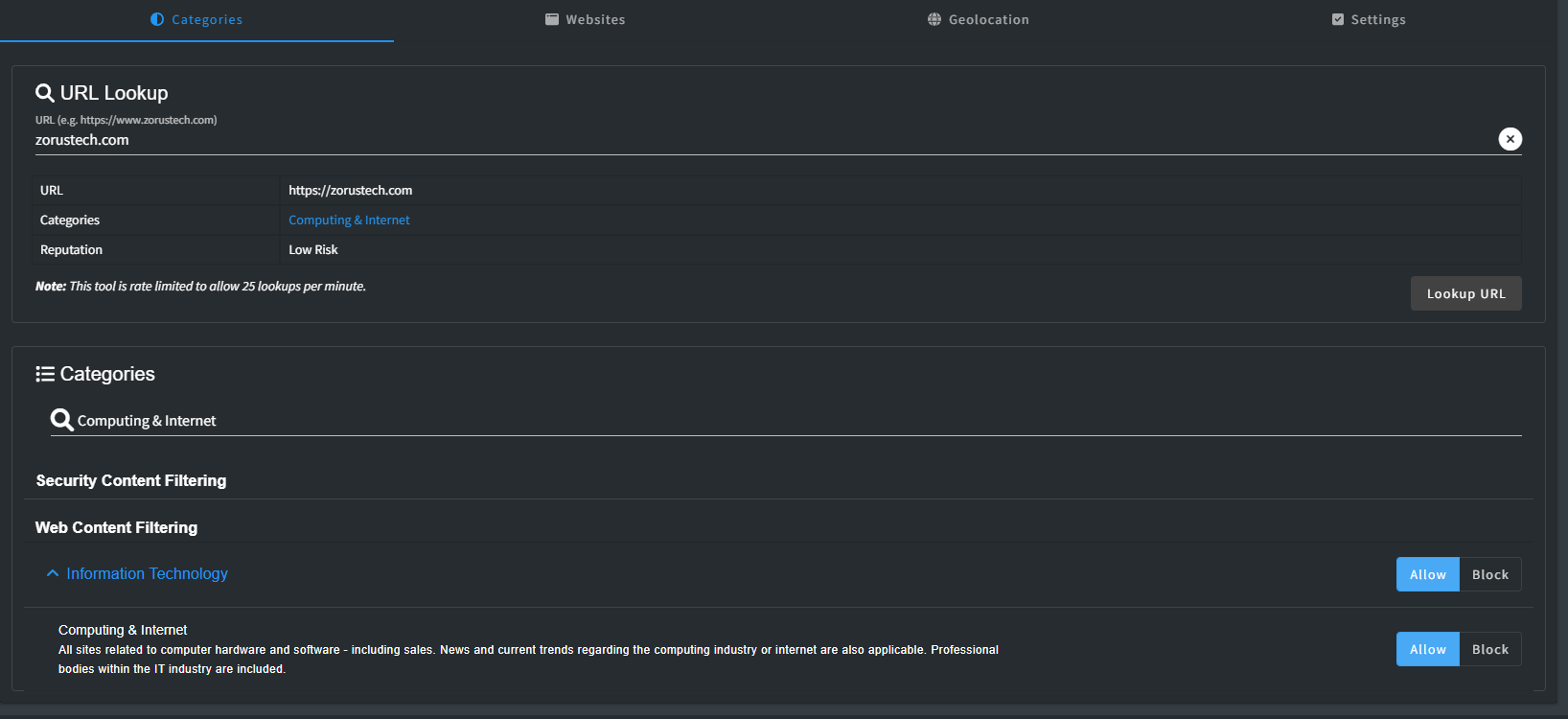
URL Lookup
If you're uncertain about a website's category, you can use the URL Lookup tool to promptly determine its classification. It provides a clickable link to the relevant Category setting, allowing you to make any necessary adjustments.
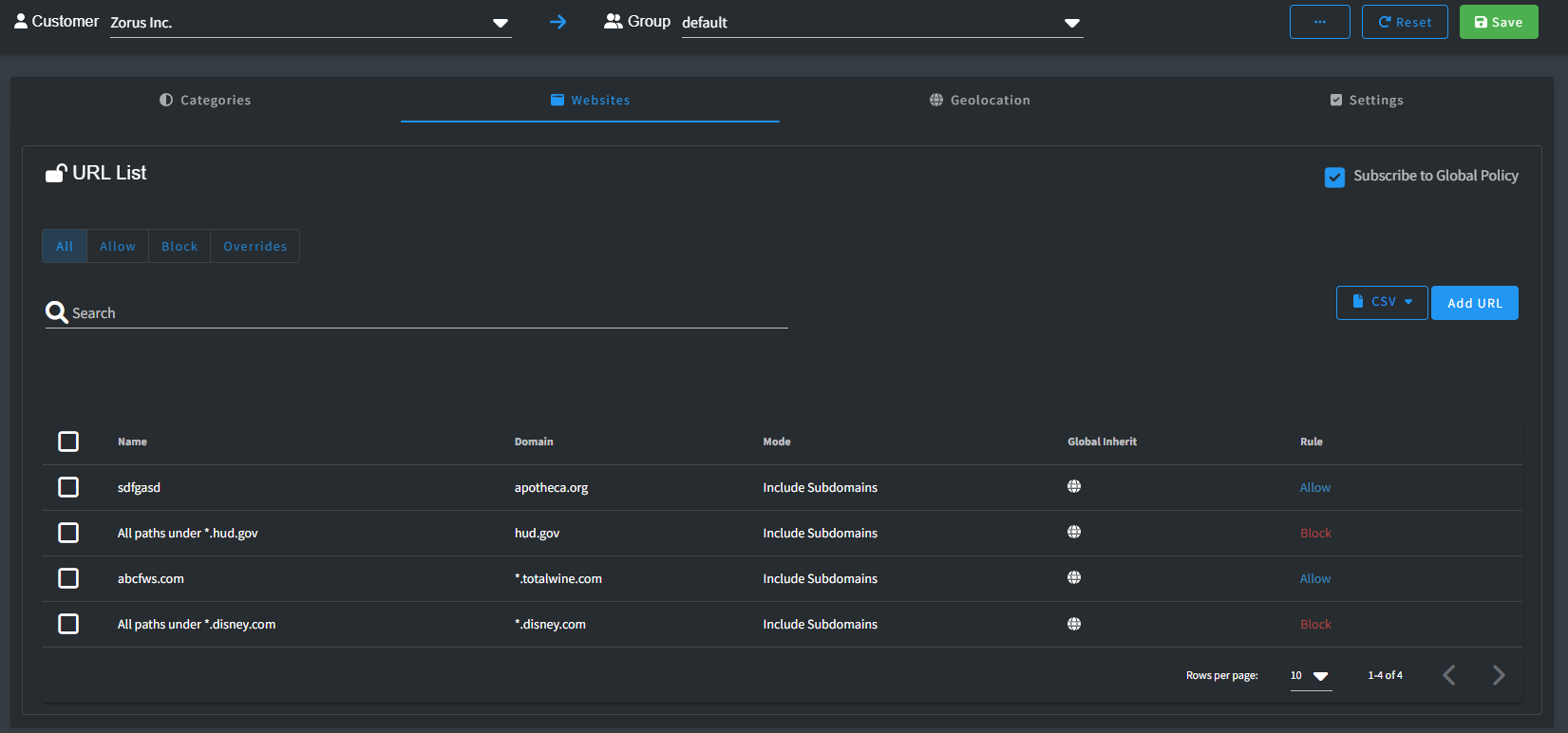
Websites
The Websites allows you to designate domains as either "Allow" or "Block." These settings dictate whether users are granted access to or restricted from visiting specific websites.
Keep in mind that the Website list holds priority over all other policy settings. Any domains listed here with Allow or Block status will consistently enforce that decision, regardless of other policy configurations.
It is important to note is that domains placed on the Allow list in this section bypass our security threat intelligence screening. While they are accessible, they are not scrutinized for potential security risks.
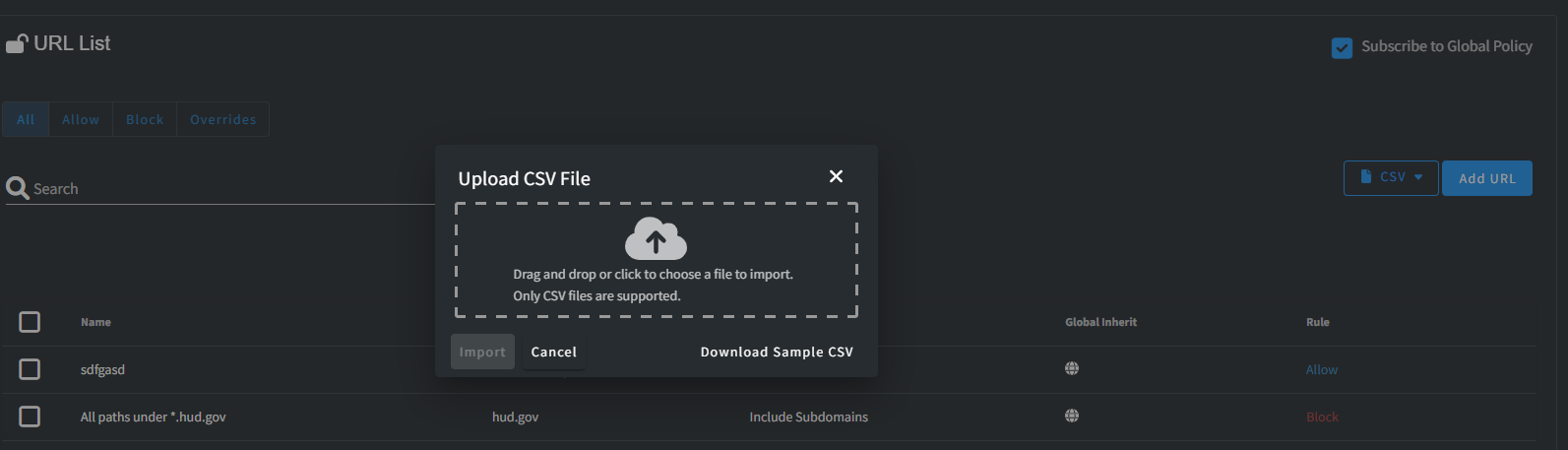
CSV Import / Export
In the Website configuration, you have the convenient option to Import or Export URLs using CSV files. To assist you, we've provided a Sample CSV right on the Import screen, which can guide you if you're uncertain about the format.
After successfully importing, you gain the advantage of making bulk modifications to various settings according to your requirements.
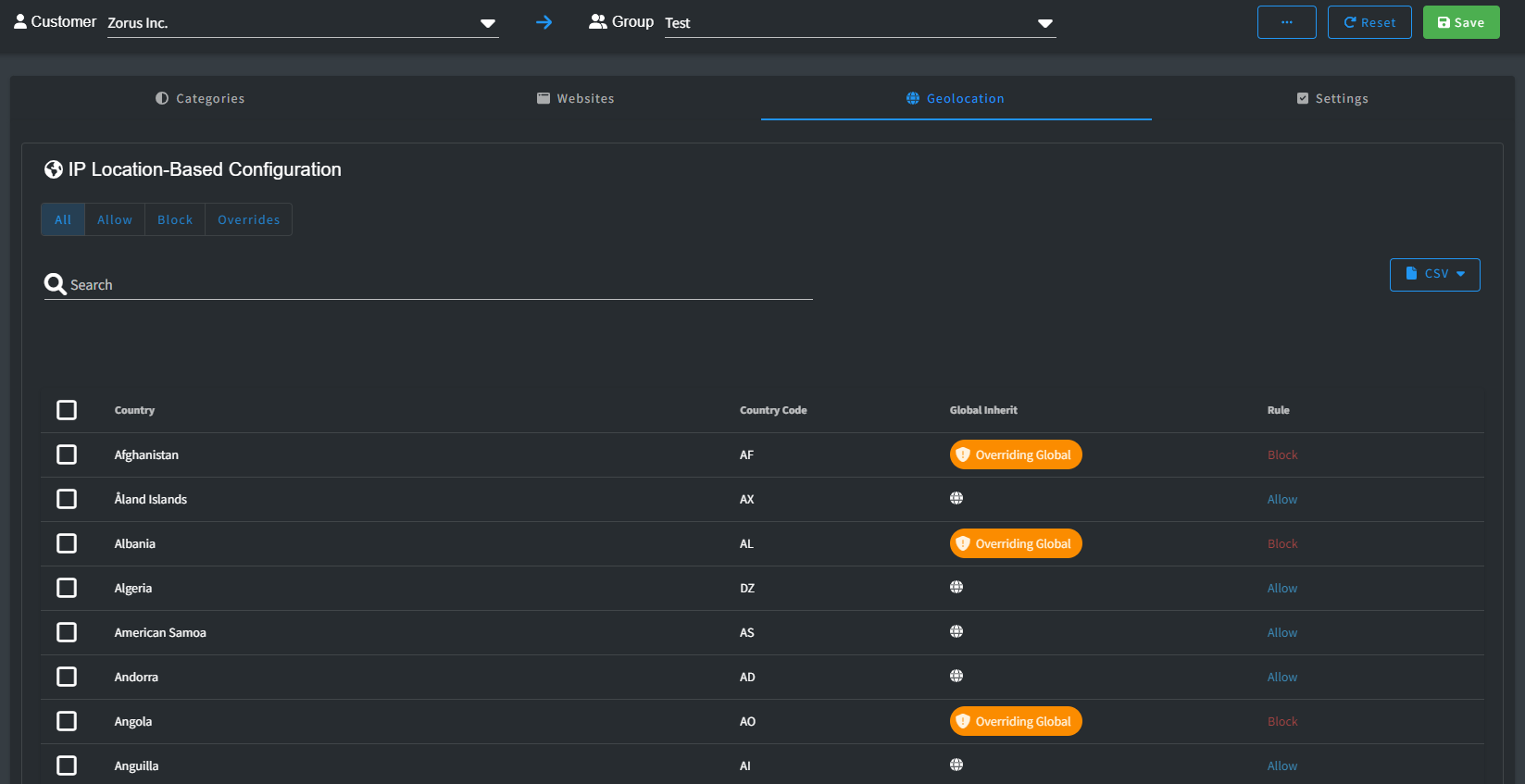
Geolocation
Geolocation functionality provides you with IP-based filtering options, allowing you to determine whether a domain is accessible based on its geographical location. With this feature, you can either permit or restrict access to websites depending on where their IP addresses are registered.
You have the flexibility to use this capability in various ways. For instance, you can choose to block countries known for high cyber threat activities, such as Russia or China. Alternatively, you can adopt a Zero Trust policy, gradually allowing access from countries as you assess their safety and reliability over time.
It's important to keep in mind that Zorus doesn't control the actual location where a domain's IP resolves. Due to the complex web infrastructure that includes services like Cloudflare and AWS, unexpected outcomes can arise. If you opt for a Zero Trust approach, be prepared for potential unblock requests from your customers. This process ensures a thorough assessment of each request to maintain a secure online environment.
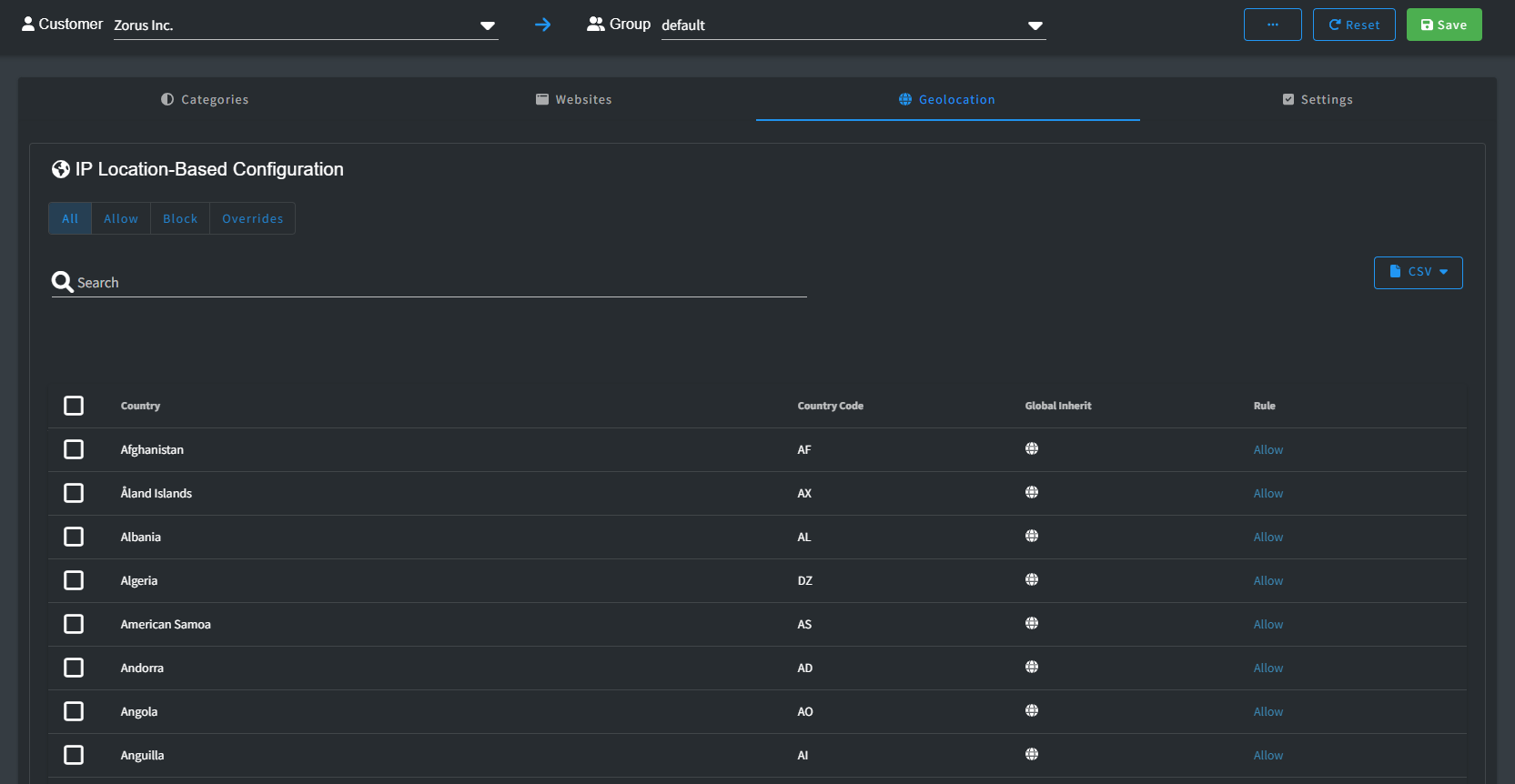
By default, all countries are allowed access. However, you have the ability to modify this default setting through the in-app bulk editor or by using CSV Import.
It's worth noting that the top-level domain (TLD) of a website doesn't necessarily determine where its IP address is located. For example, a website with a Russian .ru TLD might actually be hosted in France, allowing access from that country.
Should you wish to further refine access by allowing or blocking sub-domains for a specific country, you'll need to include the corresponding TLD record in your Websites list. This step ensures precise control over your access policies.
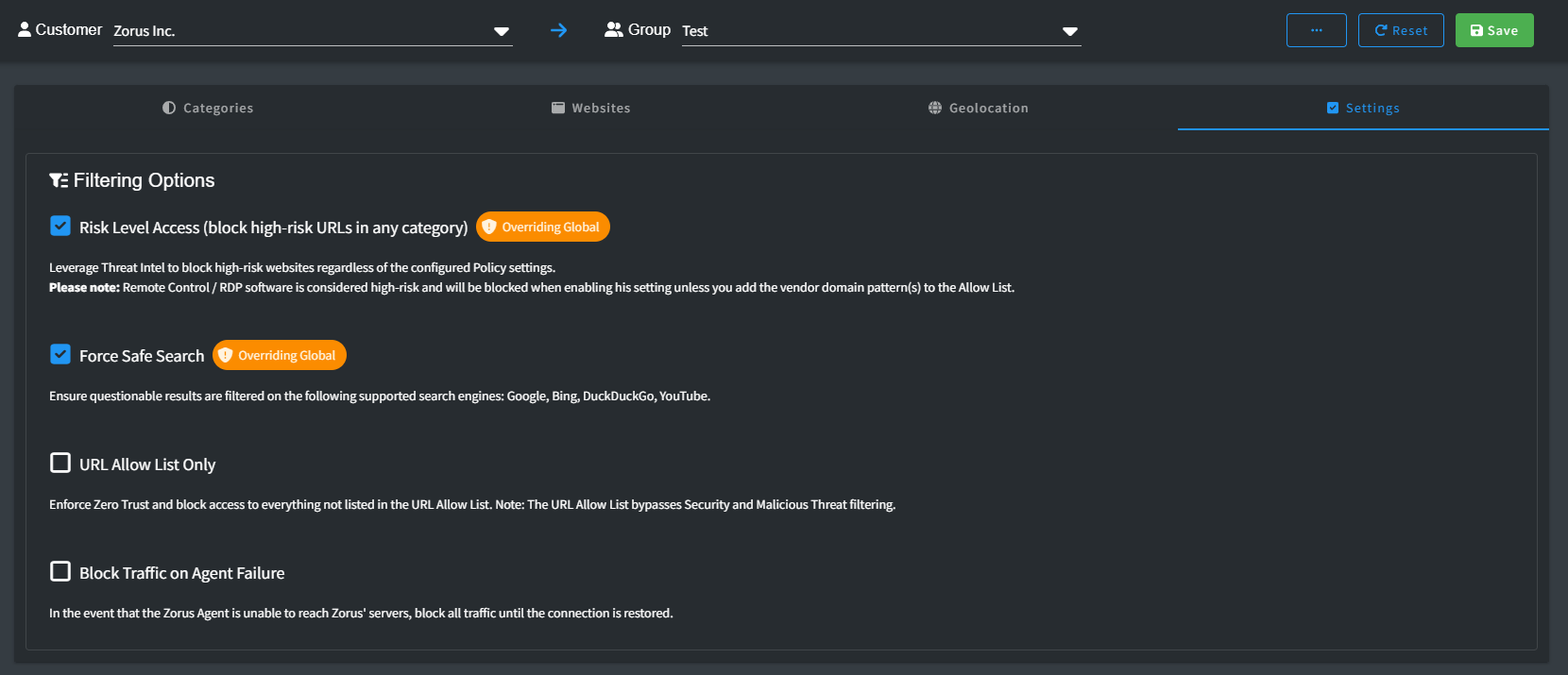
Settings
Filtering settings offer you a range of options that you can easily toggle on or off according to your preferences.
-
Full URL Filtering: Block browser-based threats by inspecting full URLs, IP addresses, and download links before pages or files load. Requires the CyberSight Browser Extension to be installed. Explore Full URL and IP Browser Filtering
WARNING! URL scanning may briefly display a blank redirection page, especially on slower connections.
- Block Unclassified Domains: Block access to unclassified domains, which have yet to be categorized by threat intelligence or added to the newly registered domains list.
WARNING! Enabling this setting may block access to local network resources, such as domains ending in .local. Be sure to add the appropriate domain(s) to the Allow List to prevent any unintended restrictions.
- Risk Level Access: Leverage Threat Intel to block high-risk websites regardless of the configured Policy settings.
WARNING! Software like Remote Control / RDP is seen as risky and will be blocked unless you specifically permit it by adding the appropriate vendor’s domain(s) to the Allow List.
- Force Safe Search: Ensure safer search results on supported search engines—Google, Bing, DuckDuckGo.
- Force YouTube Restricted Mode: Restricts the availability of potentially mature or objectionable content as determined by YouTube's proprietary algorithm.
- URL Allow List Only: Implement Zero Trust security and deny access to all websites that aren't explicitly approved in the URL Allow List.
WARNING! The URL Allow List takes precedence over Security and Malicious Threat filtering.
- Block Traffic on Agent Failure: If the Zorus Agent can't connect to the Policy server, all traffic will be halted until the connection is reestablished.
WARNING! Internet access will be disrupted during network issues, significant product maintenance windows, or if your ISP introduces latency.

Isolation
Zero Trust Device Isolation establishes rigorous controls over inbound and outbound traffic at the OS level for endpoints, limiting communication exclusively to your pre-configured allowed addresses for remote device management.
Allowed Addresses are the Domains and IP/CIDRs that will enable you to facilitate quarantine and remediation efforts directly on the isolated device.
Note: Zorus Traffic is always allowed on isolated devices to facilitate the commands and policy settings
When a device is isolated, all other Policy Configuration settings are ignored.
Tip! Allowed Addresses and can updated during isolation session to allow more traffic through as trust is established

- See Device Isolation QuickStart for more details
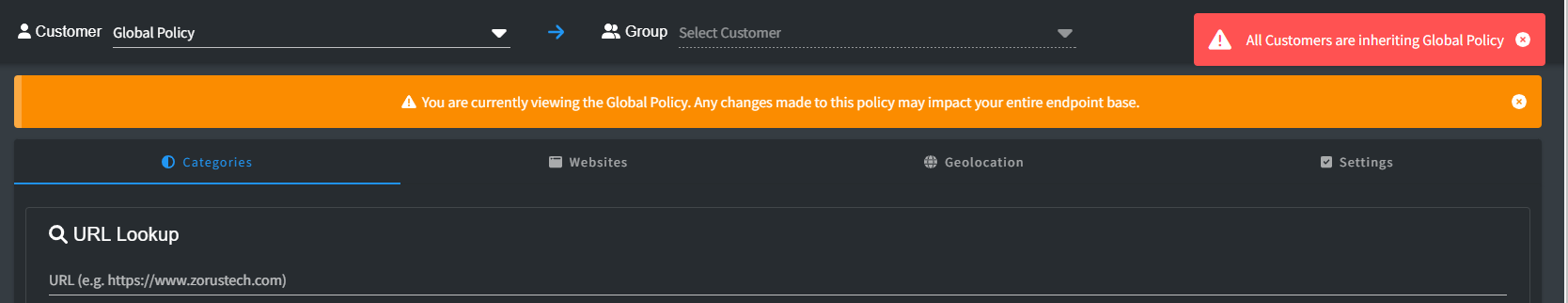
Global Policy Management
By default, all users can access the Global Policy view, accessible through the Policy Configuration option in the Zorus Portal. A warning banner appears as changes made here impact all customers. Only users with "Full Administrative Access to All Customers" and "Modify Policies" permissions can alter the Global Policy. Other users can only view it, understanding inheritance and overrides.
Different Configurations Explained:
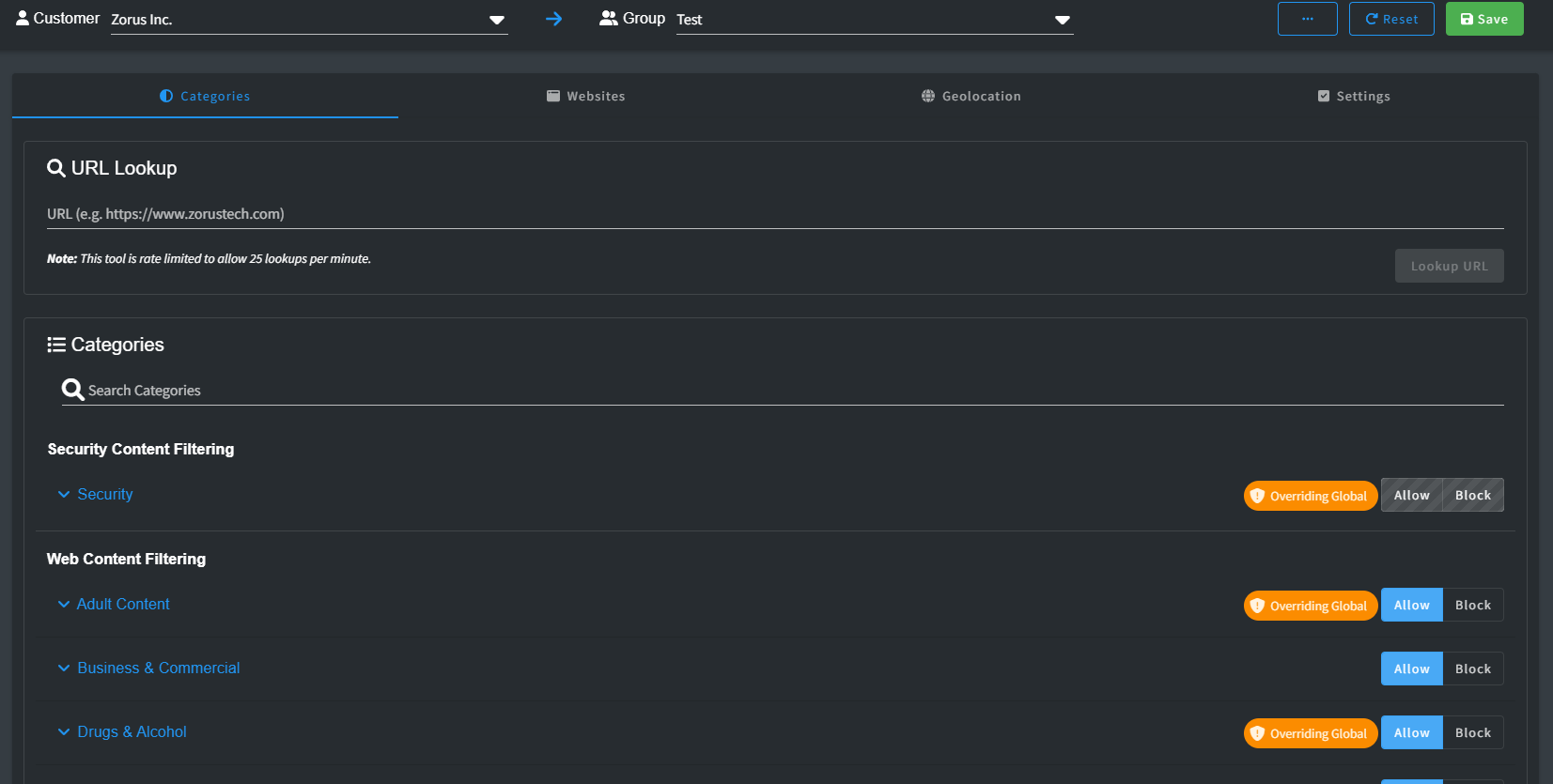
- Categories: Categories are strictly Allow or Block. Mismatched customer settings are tagged as Overriding Global. If sub-categories don't match, the parent level displays Overriding Global, expandable for details.
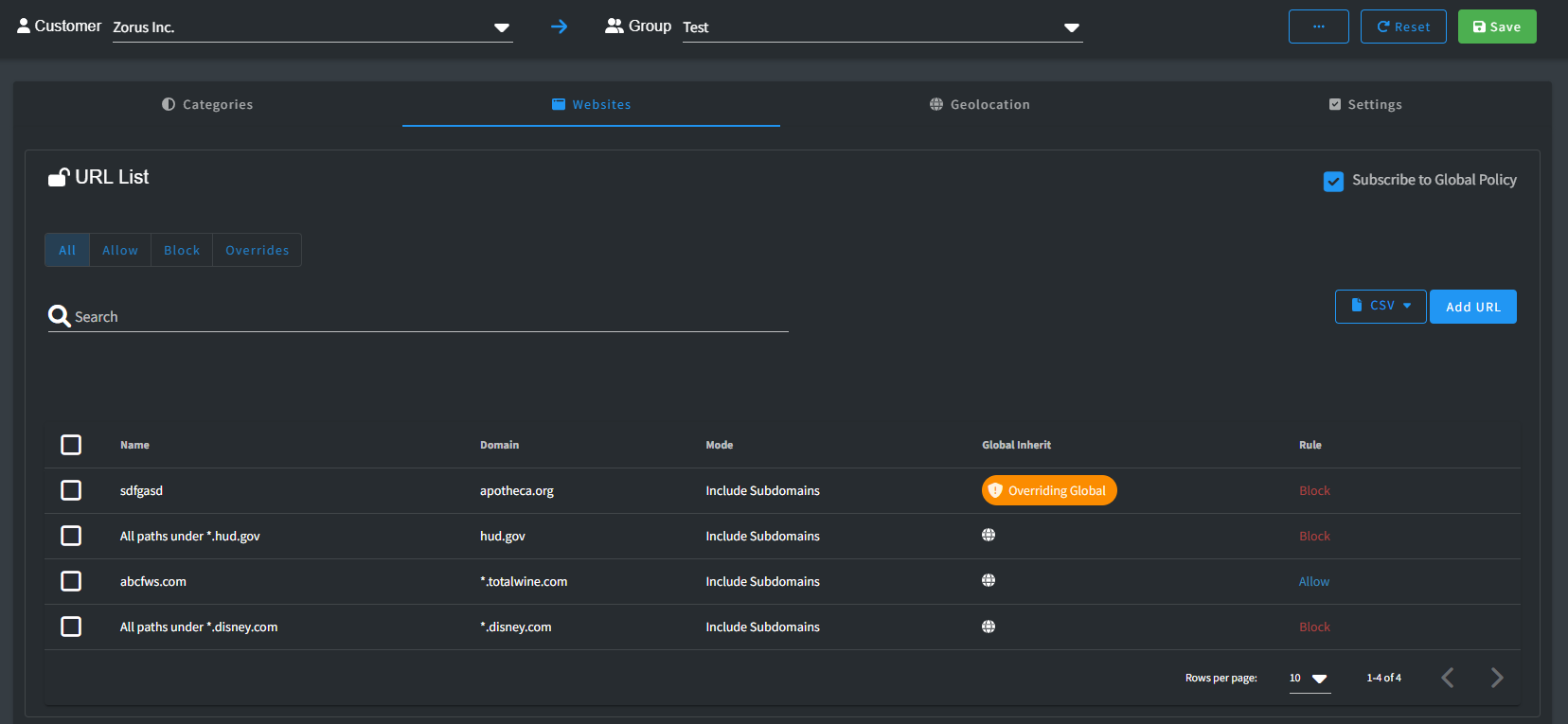
- Websites: Unique to each customer, websites offer individual configurations. Subscribing to the Global list is default, but not mandatory. Overriding a few Global list entries is possible while including the rest. Mismatched rules display Overriding Global.
- Geolocation: Countries allow only Allow or Block. Default subscribes to Global; any change is an override, indicated by Overriding Global.
- Settings: On/off settings resemble Categories. Mismatched rules show Overriding Global.
- Isolation: All Policies Subscribe to Global Allowed Addresses by default. If a Policy unsubscribes from Global, it is considered overridden. Resetting will recheck the Subscribe checkbox.
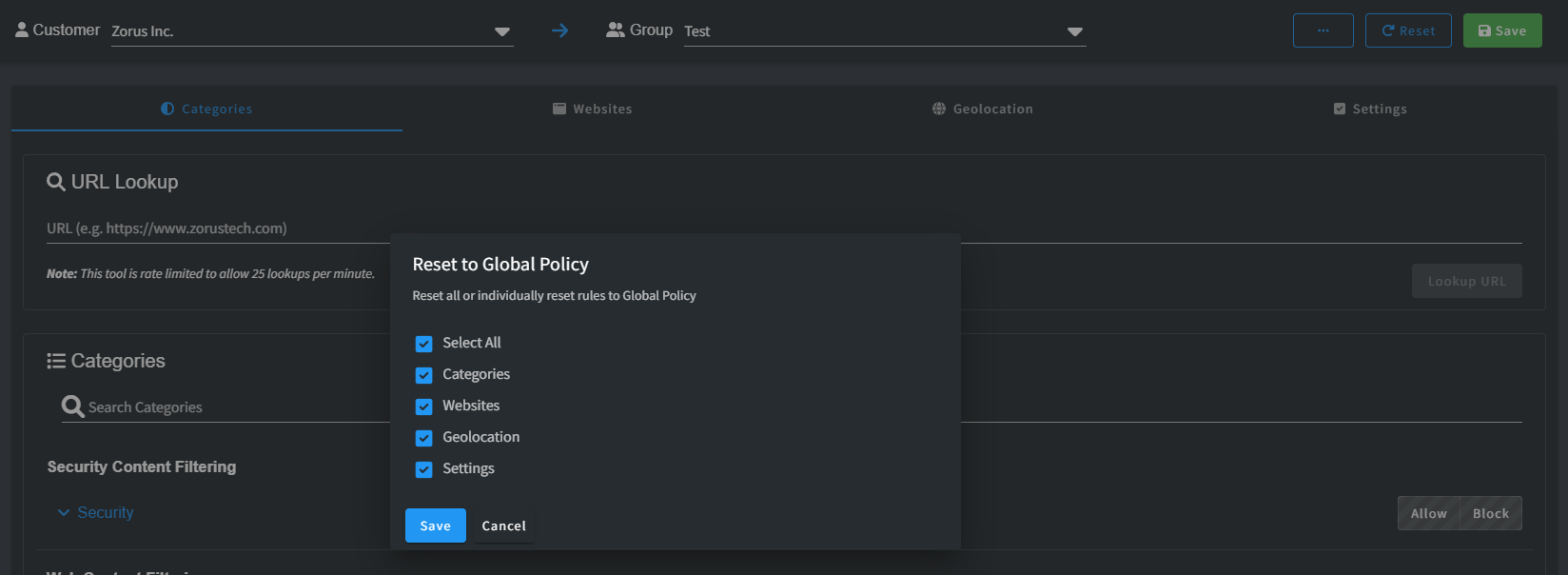
Resetting to Global Policy:
Reset option restores customers to Global Policy, individually or in bulk. At the Customer Group level, it aligns specific options with Global Policy settings.
At the Global Policy level, it resets multiple customers at once. Important Note: Resetting triggers immediate change. For Websites, Reset also ensures "Subscribe to Global Policy" is checked.
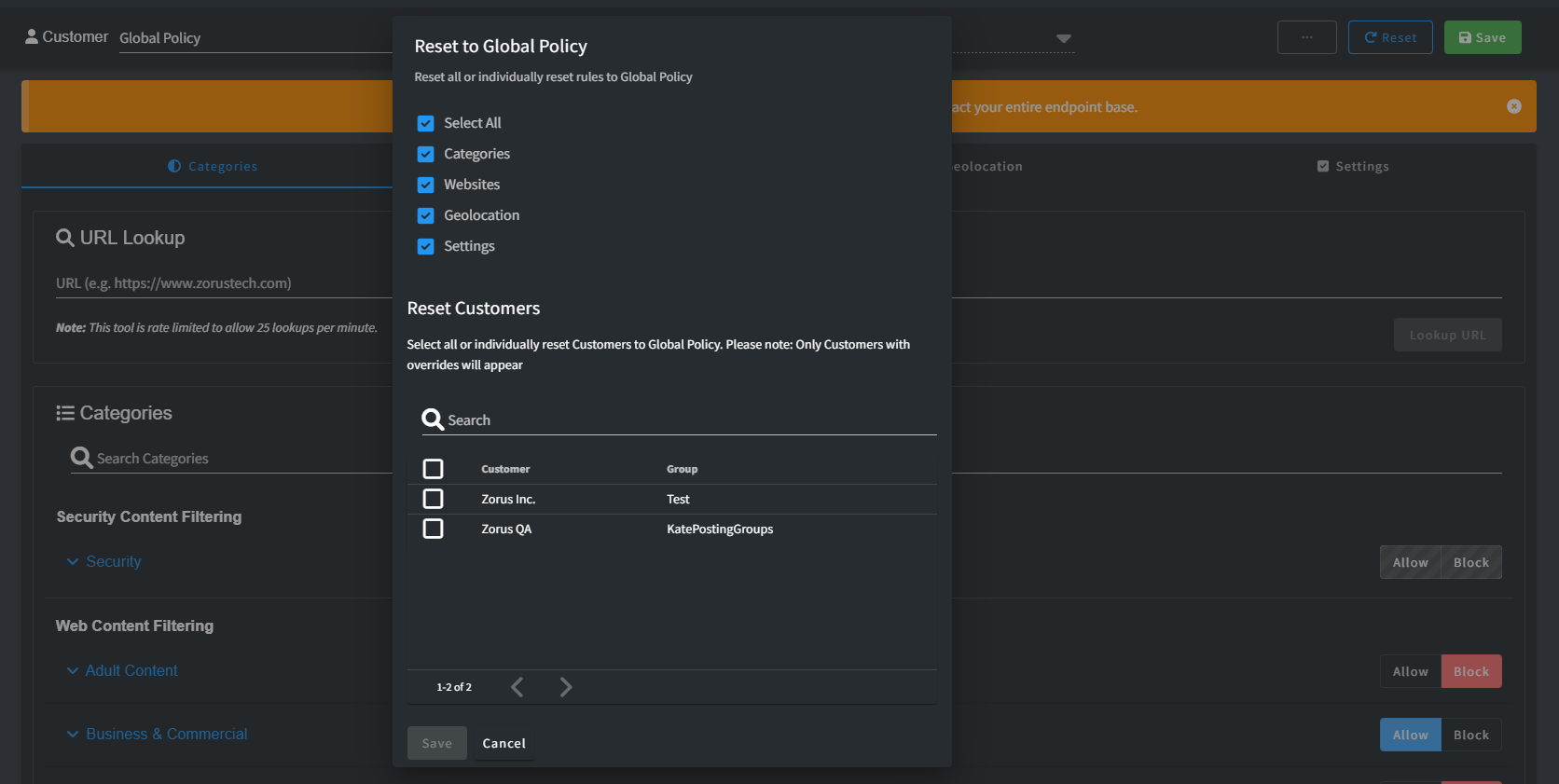
If a all Customer policies match Global entirely, an error indicates no overrides.