Browse: Traffic Logs
Examine DNS traffic and effortlessly export limited datasets for further analysis
 Traffic Logs
Traffic Logs
Analyze DNS traffic with precision by narrowing down your search to specific date and time intervals, conveniently adjustable in 15-minute segments.
Easily export selected datasets in CSV format for seamless integration with other tools or for further in-depth analysis.
Enhance traffic logs with Full URL information using the CyberSight Browser Extension, bolstering incident response capabilities for superior troubleshooting and security forensics.
Note: Due to the significant volume of daily DNS requests received, access to traffic logs is restricted to one customer at a time.
Date/Time Filters
By default, traffic logs are set to display data for the current day between 8:00 AM and 6:00 PM local time for the logged-in user.
There is a checkbox option to quickly expand the time range to All Day
The user interface (UI) is designed to accommodate a maximum of two weeks' worth of data. For more extensive datasets, users can extract the required information from the Report Manager via the Endpoint Traffic Logs report for up to 30 days.
Tools
- CyberSight Logs (Full URL Context)
- Utilize the CyberSight Browser Extension to gain precise visibility into the websites accessed by users, enhancing troubleshooting and security forensics in incident response
- CyberSight Logs Toggle: Enable or disable Full URLs in your Traffic Logs, including Quick Filter searches. (Requires CyberSight Browser Extension installation)
- Export to CSV: Full URL records from CyberSight are seamlessly integrated into your Traffic Logs export, labeled as Event: CyberSight; Allow/Block: URL Event
- Use Cases:
- Troubleshooting: Identify and address issues like broken links or slow-loading pages swiftly by pinpointing the exact paths users took, facilitating the determination of root causes
- Context: Enhance incident response forensics by tracing user paths through websites, aiding in the identification of malicious domains or resources. Gain a clearer understanding of the incident's scope, attack vectors, and implement effective countermeasures to mitigate future risks
- Utilize the CyberSight Browser Extension to gain precise visibility into the websites accessed by users, enhancing troubleshooting and security forensics in incident response
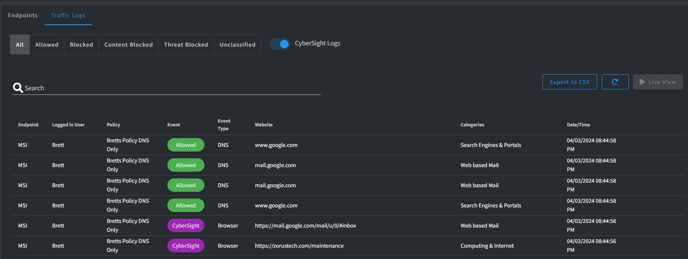
- Quick Filters
- All - All captured DNS requests based on current filter
- Allowed - DNS requests allowed based on current filtering
- Blocked - DNS requests blocked based on current filtering
- Content Blocked - Total number of DNS records blocked by Policy configuration
- Categories: Web Content Filtering, Application Filtering
- Websites: Block List
- Geolocation: Block List
- Settings: Unclassified Domains, URL Allow List Only
- Content Blocked - Total number of DNS records blocked by Policy configuration
-
-
- Threat Blocked - Total number of high risk DNS records blocked:
- Categories: Security Filtering
- Settings: Risk Level Access (high-risk URLs)
- Malicious Domain List
- Threat Blocked - Total number of high risk DNS records blocked:
- Unclassified - DNS requests with no categorization by Threat Intel providers
-

- Export to CSV - export the records to CSV for further analysis
Export to CSV routes user to the Report Library pre-populated to execute the file generation process
- Refresh - get latest DNS requests based on current filtering
- Toggle Live View - view new incoming traffic every 10 seconds to assist in live diagnostics
Note: Date/Time Filters must be include the current date and time or button is disabled
Grid Columns

- Endpoint - Name of Endpoint
- Logged in User - User logged on when the DNS record was sent
- Policy - Name of Policy Endpoint is using for Filtering decisions
- Event - Whether DNS was Allowed / Blocked
- Hover state displays Filtering reason
- Website - The fully qualified domain name (FQDN) of the the DNS request
- Categories - The category the Website is classified as by our Threat Intel
- Date/Time - The relative time the DNS request occurred
- Hover state displays complete date/time
- Actions
- Add to Policy - add the Website to Customer or Global Policy
- Report Miscategorization - report incorrect categorization of Website to our Threat Intel
- Ellipsis
- View Log Entry - view deeper details about the individual DNS request
- View Policy - view / edit applied Endpoint Policy

